Cybersecurity researchers have uncovered a widespread malware campaign where hackers distribute a dangerous infostealer called TamperedChef through fraudulent PDF editing software promoted via Google Ads. This sophisticated operation has been ongoing for months, leveraging multiple domains, fake certificates, and ad campaigns to trick users into downloading malicious tools disguised as legitimate apps.
The malicious activity was first observed in a fake application named AppSuite PDF Editor, a program heavily promoted across various websites starting in late June. According to cybersecurity firm Truesec, the app appeared harmless at first, functioning like a typical PDF tool. However, researchers noted that on August 21, an update activated hidden components that turned the app into a fully operational infostealer.
The malware is delivered when the app’s executable runs with the “-fullupdate” argument. Once active, TamperedChef checks for security software installed on the system and leverages Windows DPAPI (Data Protection Application Programming Interface) to extract encrypted credentials, session cookies, and other sensitive data stored in browsers. This makes it a direct threat to online accounts, financial services, and personal data.
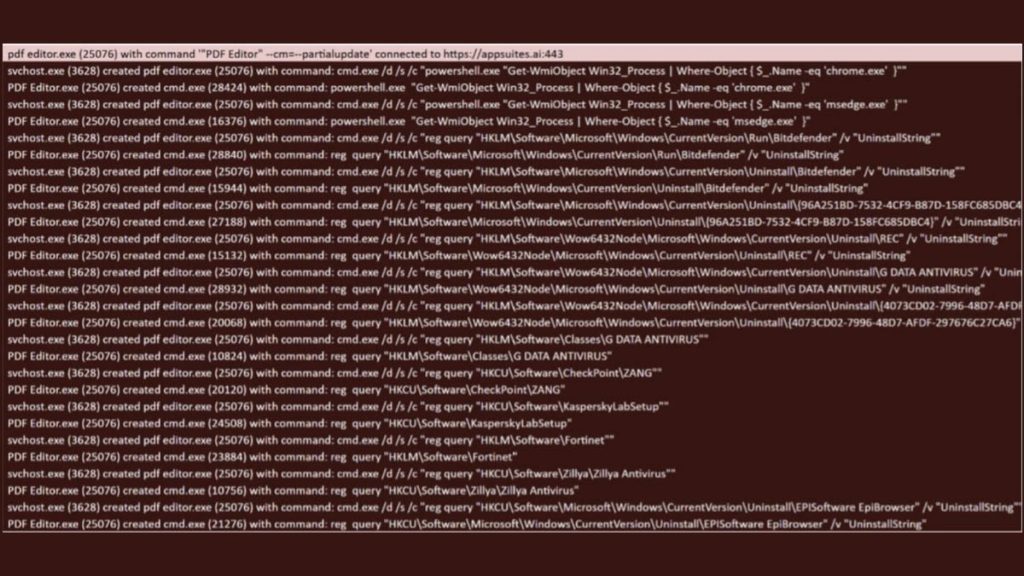
source: Truesec
Investigations revealed that the threat actors used Google Ads campaigns to boost visibility and lure unsuspecting victims. Truesec researchers discovered at least five distinct ad campaign IDs, suggesting a large-scale distribution strategy. The malware operators appear to have timed the release carefully, activating the infostealer component only after the campaigns had been running for weeks, maximizing downloads before Google’s standard 60-day ad expiration period.
Adding to the deception, the applications were signed with fraudulent certificates from at least four companies, including ECHO Infini SDN BHD, GLINT By J SDN BHD, and SUMMIT NEXUS Holdings LLC. This allowed the software to appear trustworthy, bypassing security checks that would normally block unsigned executables.
The operation extended beyond just stealing data. According to additional analysis by Expel, some versions of the PDF Editor and related apps, including OneStart and ManualFinder, attempted to enroll infected devices into residential proxy networks. This tactic effectively hijacks a victim’s internet connection, making it available for use by other malicious actors.
In certain cases, users were explicitly prompted to allow their devices to be used as proxies in exchange for free access to the PDF tool. While this may seem optional, the behavior is closer to malware and adware practices, raising red flags for cybersecurity professionals.
Conclusion
The TamperedChef campaign highlights the growing risks of downloading software from advertisements and unverified sources. By combining fake certificates, ad-driven distribution, and staged activation, attackers successfully avoided early detection while infecting large numbers of systems. Both Truesec and Expel have released indicators of compromise (IoCs) to help defenders protect their networks, but the campaign demonstrates how cybercriminals are becoming more creative in weaponizing legitimate-looking software. Users and organizations alike should remain vigilant, only download software from trusted sources, and regularly audit systems for suspicious processes.





