eSIM Security Shaken by Major Breakthrough
In a development that’s raising alarms across the telecom and cybersecurity industries, Security Explorations, a renowned cybersecurity lab, has successfully hacked a GSMA-certified eSIM — the Kigen eUICC card, believed to be one of the most secure in the market. This eSIM module is based on Java Card technology and had EAL4+ security certification, memory protection, and several other safeguards. Yet, researchers were able to gain full control over the card, revealing severe weaknesses in its architecture.
Not Just a Vulnerability — A Critical Breach
The exploit targets known issues in Java Card bytecode execution, particularly vulnerabilities that have been flagged since 2019. These issues stem from flaws in data type processing, found both in Oracle’s implementation and in Kigen’s card.
Using custom automated tools, Security Explorations analyzed bytecode logic, memory usage, stack handling, and variables to conduct deep inspection and penetration testing. These tools uncovered that the Kigen eUICC architecture allowed attackers to bypass key security barriers, paving the way for a successful real-world exploit.
How the eSIM Was Hacked
The researchers demonstrated a fully functional attack scenario, wherein they installed a malicious Java application via SMS. This gave them access to extract the ECC private key — a cryptographic key that unlocks access to eSIM profiles from major operators including AT&T, Vodafone, Orange, and T-Mobile.
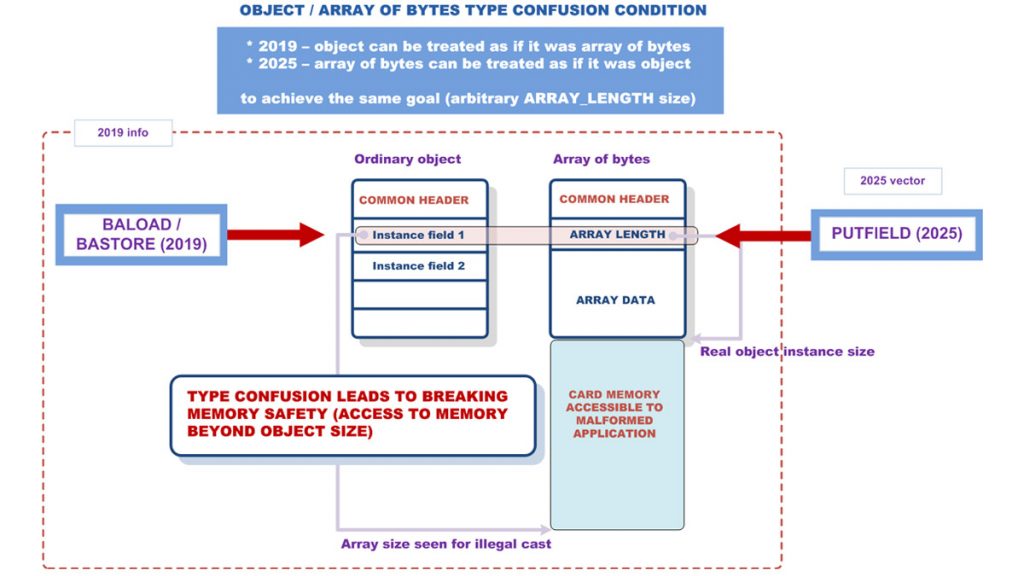
Once compromised, these profiles — which include network configurations, OTA keys, applets, and subscriber metadata — could be cloned, altered, or reinstalled. Worse still, the network operator had no way to detect this compromise, making it an undetectable breach.
In one instance, an attack on Orange’s network showed that calls and SMS could be redirected to a cloned device. The original user remained unaware, while the clone received all communications — a textbook example of an invisible interception.
Industry Response and Consequences
Kigen has since acknowledged the vulnerability and paid a $30,000 bounty to Security Explorations. Meanwhile, GSMA has amended its TS.48 specification, now banning the installation of Java apps on test profiles, to help prevent similar exploits.
The research also tested other eSIM cards. A chip from Giesecke+Devrient withstood all attacks. However, due to NDAs and restricted access, other vendors’ cards could not be fully analyzed.
On the server side, the results were equally troubling. Security Explorations revealed that back-end systems from IDEMIA and Thales failed to reject certificates from compromised eSIMs. These servers — critical for eSIM authentication and provisioning — lacked proper validation mechanisms, enabling cloned or hijacked profiles to go undetected.
Implications for Telecom and Cybersecurity
This exploit isn’t just a theoretical concern — it has real-world, scalable consequences. Telecom operators now face increased risk of invisible SIM cloning, data interception, and unauthorized network access. The fact that these vulnerabilities existed in certified “secure” eSIMs underscores how compliance does not equal security.
Conclusion: Time for a Rethink in eSIM Security
The hack of Kigen’s GSMA-certified eSIM card by Security Explorations is a wake-up call for the global telecom and cybersecurity community. It reveals that security certifications are not infallible and that proactive vulnerability research is essential. With cloned eSIMs capable of infiltrating mobile networks invisibly, stakeholders — from chipmakers to carriers — must rethink how trust is built and verified in a rapidly digitizing mobile world.
SEO Keywords:
SEO Meta Description:






