A Growing Threat to WordPress Site Owners
More than 200,000 WordPress websites are exposed to hijacking attacks due to a critical vulnerability in the Post SMTP plugin, a tool widely used for managing email delivery on WordPress. With over 400,000 active installations, Post SMTP serves as a robust alternative to the built-in wp_mail() function—until now.
Understanding the Vulnerability
The issue, now cataloged as CVE-2025-24000, stems from a flaw in the plugin’s REST API endpoints. This bug, reported on May 23 by a security researcher and analyzed by the cybersecurity firm PatchStack, arises from broken access controls. Specifically, the plugin fails to verify a user’s privilege level, only checking whether the user is logged in.
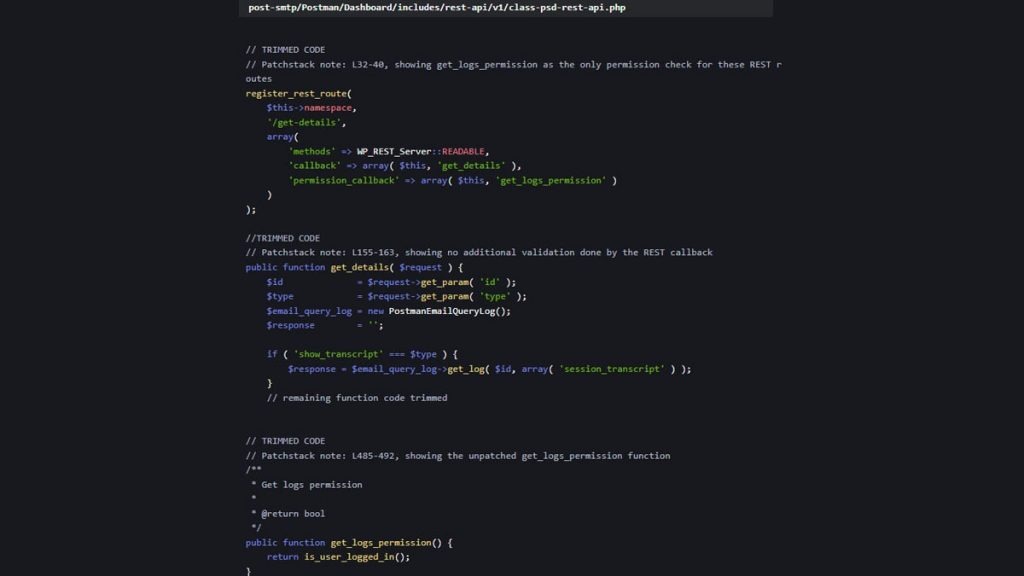
This opens a dangerous loophole. Even low-level users like Subscribers could access sensitive email logs, including full email content. In a worst-case scenario, a Subscriber could trigger a password reset for an Admin, retrieve the reset link from the logs, and take over the administrator account—a straightforward path to a full site compromise.
Developer Response and Patch Release
Upon being alerted, Post SMTP’s developer, Saad Iqbal, quickly took action. By May 26, a fix was submitted and later approved by PatchStack. The solution involved adding privilege checks within the get_logs_permission function to ensure only properly authorized users can access sensitive data.
This security patch was released in Post SMTP version 3.3.0 on June 11, 2025. However, despite the severity of the vulnerability, many site owners have yet to act.
Why 200,000+ Sites Are Still Vulnerable
According to WordPress.org statistics, only 48.5% of users have upgraded to the safe 3.3.0 version. A significant number—about 96,800 websites—still run on the older 2.x versions, which also contain other unpatched vulnerabilities. This leaves a vast portion of the internet dangerously exposed.
What Site Owners Should Do Now
If you’re using the Post SMTP plugin, it’s critical to immediately update to version 3.3.0 or later. Delaying this exposes your site to potential admin account hijacking, data theft, and malicious injections that can destroy trust and affect SEO rankings. Additionally, consider running regular security audits and using a trusted WordPress firewall or monitoring plugin to detect unusual user behavior.
Conclusion
This incident highlights the importance of keeping WordPress plugins updated and maintaining least-privilege access controls. With over 200,000 websites at risk, the CVE-2025-24000 flaw in Post SMTP is not just another warning—it’s a call to action for site administrators everywhere. Proactive maintenance is no longer optional; it’s essential for the safety of your site, your users, and your business.






