A new and highly sophisticated cyber threat has emerged from North Korea, as state-backed hackers have begun exploiting blockchain technology in an unprecedented way. Researchers from Google Threat Intelligence Group (GTIG) have identified that a North Korean threat actor, tracked internally as UNC5342, is using a technique known as EtherHiding to embed and distribute malware via smart contracts on public blockchains such as Ethereum and Binance Smart Chain. This represents the first known instance of a state-sponsored hacking group utilizing blockchain infrastructure for malware hosting and delivery.
First documented by Guardio Labs in 2023, EtherHiding involves embedding malicious payloads directly within smart contracts. These payloads can be retrieved later using read-only blockchain queries, allowing hackers to deliver and update malware without leaving visible on-chain traces. This approach gives threat actors anonymity, resilience to takedowns, and near-zero operational costs, making it an ideal vehicle for stealthy and persistent attacks.
According to GTIG, the North Korean group has been employing EtherHiding since February 2025 in operations known as Contagious Interview, a social engineering campaign that targets software developers and web engineers with fake job opportunities. Attackers impersonate legitimate tech firms—such as BlockNovas LLC, Angeloper Agency, and SoftGlide LLC—to lure victims into running malicious code during a supposed “technical assessment.”
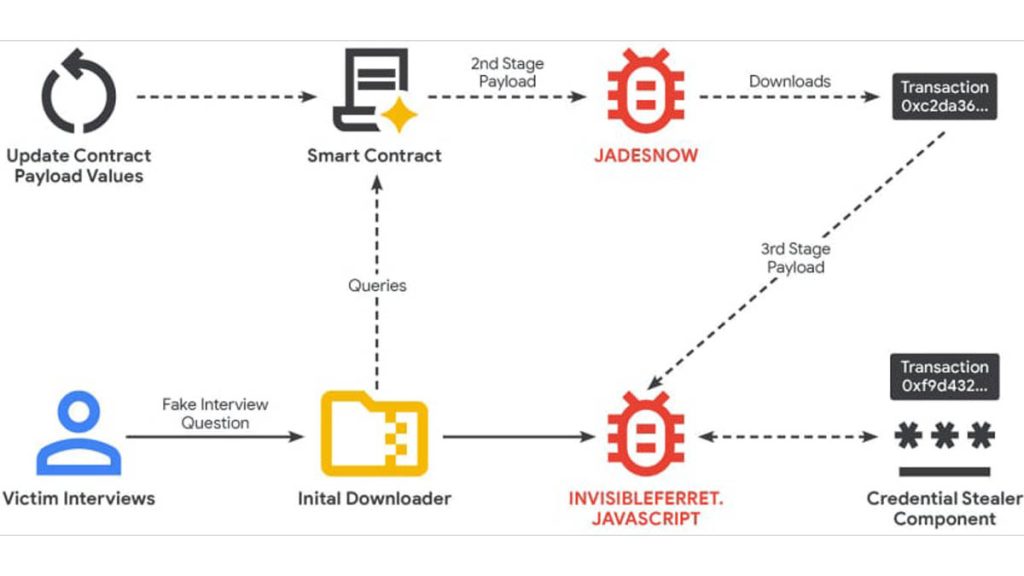
Once the code is executed, it launches a JavaScript downloader that communicates with the blockchain to retrieve further malicious payloads. One of the key components observed in these operations is the JADESNOW downloader, which interacts with Ethereum smart contracts to fetch the next-stage malware—a JavaScript variant of the InvisibleFerret spyware, built for long-term espionage and data theft.
GTIG reports that this multi-stage infection chain allows attackers to update campaign configurations cheaply and frequently. “The transaction details show that the contract has been updated over 20 times in four months, with each update costing roughly $1.37 in gas fees,” the report states. This makes campaign adaptation and payload rotation both cost-effective and extremely difficult for defenders to monitor.
The malware is capable of running entirely in memory, evading detection tools while executing commands from its C2 (command and control) server. It can steal credentials, credit card data, and cryptocurrency wallet details from popular browsers like Chrome and Edge. The credential-stealing module specifically targets wallets such as MetaMask and Phantom, posing severe risks to crypto investors and Web3 developers.
Cybersecurity experts warn that EtherHiding marks a major tactical shift in how state actors exploit blockchain immutability for cyber-espionage. Using multiple blockchains for payload retrieval—something rarely seen—may indicate segmentation within North Korean cyber operations, with different teams specializing in Ethereum and BNB Smart Chain ecosystems.
GTIG advises users and enterprises to treat unsolicited job offers with extreme caution, especially those that involve code execution or downloads. Administrators should restrict risky file types (.EXE, .DLL, .BAT, .MSI), enforce strict browser policies, and regularly audit blockchain-related network traffic to mitigate exposure.
Conclusion:
The adoption of EtherHiding by North Korean hackers is a worrying escalation in cyberwarfare tactics, blending blockchain innovation with state-sponsored espionage. By exploiting the decentralized nature of smart contracts, these attackers gain stealth, persistence, and flexibility that traditional cybersecurity defenses struggle to counter. As blockchain technology continues to evolve, so too must global strategies for monitoring and defending against on-chain malware campaigns.






