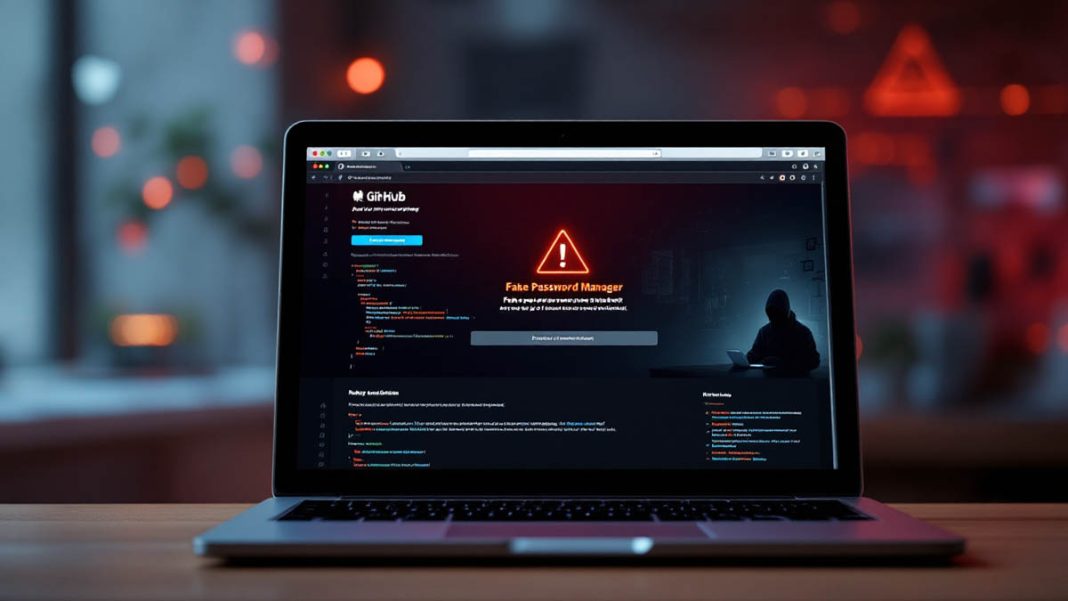
A new cybersecurity threat is making waves in the Apple ecosystem, as LastPass has issued a warning about a campaign targeting macOS users with malicious apps disguised as trusted software. The attackers behind this scheme are using fraudulent GitHub repositories to trick unsuspecting users into downloading malware, specifically the Atomic macOS Stealer (AMOS).
This malware is not new to the scene. AMOS is part of a malware-as-a-service (MaaS) operation available for $1,000 per month, commonly used to steal sensitive data from infected machines. However, in its latest iteration, developers have added a backdoor feature, giving hackers persistent, stealthy access to compromised systems. This makes the campaign particularly dangerous, as victims may remain unaware that their devices are under constant surveillance.
The scope of impersonation in this campaign is staggering. Apart from LastPass, the attackers have created fake versions of more than 100 widely used applications, including 1Password, Dropbox, Confluence, Robinhood, Fidelity, Notion, Audacity, Adobe After Effects, Thunderbird, and SentinelOne. By setting up countless deceptive GitHub repositories optimized with SEO tactics on Google and Bing, they ensure that these malicious files appear legitimate and rank high in search results.
The attack method being used is known as a ClickFix attack. Victims visiting these fake repositories encounter a download button that redirects them to a secondary site. There, they are instructed to paste a command into the macOS Terminal. While this may look harmless to inexperienced users, the command executes a curl request to fetch a base64-encoded URL, which then drops the AMOS payload—named install.sh—into the /tmp directory. From that moment, attackers gain control over the system, harvesting valuable information and maintaining hidden access.
This technique is not unique to this campaign. Similar ClickFix attacks have been reported in the past, including fake software impersonating Booking.com or ads promoting fraudulent fixes for macOS-related issues. The challenge lies in the fact that even when repositories are reported and taken down, attackers can quickly create new ones through automation and fake accounts.
For users, the best defense is vigilance. Cybersecurity experts stress that people should never run Terminal commands they don’t fully understand. When downloading applications, it’s essential to rely only on official vendor websites or reputable community-backed sources. If a macOS version of a product isn’t offered by the legitimate company, chances are that any “unofficial” port is malicious.
In conclusion, this campaign highlights how attackers combine SEO manipulation, fake repositories, and social engineering to exploit user trust. With AMOS gaining new capabilities, macOS users must be more cautious than ever. Only official sources should be trusted, and unusual installation steps should raise immediate red flags.