A new wave of cybercrime is sweeping through American universities as a group known as Storm-2657 hijacks employee salaries in what Microsoft analysts call “pirate payroll” attacks. Since March 2025, this financially motivated operation has been exploiting Workday accounts—and possibly other HR SaaS platforms—to divert salary payments into criminal-controlled bank accounts.
According to Microsoft Threat Intelligence, the attackers have already compromised 11 accounts across three universities, using them to launch phishing emails to nearly 6,000 users at 25 institutions. These emails are cleverly disguised, with lures customized to the university environment. The topics range from fake campus illness alerts and faculty misconduct notices to messages impersonating university presidents sharing urgent compensation updates.
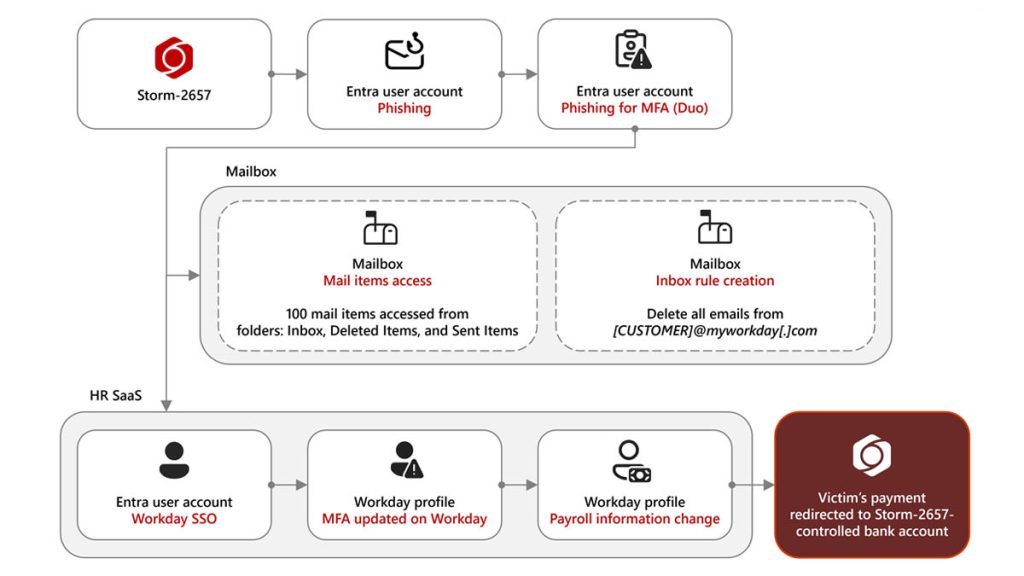
The key vulnerability, Microsoft reports, is not in the Workday platform itself, but in human error and the absence of strong multifactor authentication (MFA). Many universities still rely on non-phishing-resistant MFA, which leaves them open to adversary-in-the-middle (AITM) techniques. Once the target clicks a malicious link, the attacker steals MFA tokens, gaining access to Exchange Online and Workday accounts.
Once inside, Storm-2657 establishes persistence through email inbox rules that delete or hide Workday warning notifications. This allows the criminals to alter payroll configurations unnoticed, redirecting funds to accounts they control. Using single sign-on (SSO) access, they can silently change payment destinations and even enroll their own phone numbers as MFA devices, making it much harder for legitimate users to regain control.
Microsoft’s investigation found that after compromising initial accounts, the threat actors used them to send additional phishing waves both internally and externally, creating a chain of compromised universities. The campaign demonstrates the increasing sophistication of business email compromise (BEC) tactics—once focused on corporate executives, now expanding to higher education institutions.
Microsoft has notified affected universities and provided detailed guidance to strengthen defenses, including adopting phishing-resistant MFA, implementing conditional access policies, and enhancing user awareness training. The company stresses that these incidents underscore the urgent need for universities to modernize cybersecurity frameworks, particularly in payroll and HR systems that handle sensitive financial data.
According to the FBI’s Internet Crime Complaint Center (IC3), BEC fraud remains one of the most lucrative forms of cybercrime. In 2024 alone, the IC3 logged over 21,000 BEC-related complaints, totaling losses of $2.7 billion, second only to investment scams. Yet experts warn these figures represent only a fraction of the true scope, as many institutions do not report such incidents publicly.
In conclusion, the Storm-2657 “Payroll Pirate” campaign serves as a wake-up call for the academic sector. Universities must go beyond traditional email security measures and adopt phishing-resistant authentication, continuous monitoring, and proactive threat response to safeguard their digital and financial ecosystems against this new breed of targeted cyber fraud.






